Announcing - Fine-Grained Access Control
3/11/2025
We're excited to roll out fine-grained access control today – a feature many of you have asked for. This update lets workspace owners attach approvers directly to specific views, giving you much more control over who can approve what changes in your infrastructure. It's built on top of our existing approval workflows, but now with the precision many compliance-focused teams need.
A quick refresher on views
If you missed our Views announcement, here's a quick explainer: Views lets you organize your infrastructure components into collections that make sense for different users (developers, network engineers, security, etc.) or purposes. Think of them as custom perspectives on your system.
A networking engineer might need to see VPCs and subnets, while a developer cares more about application components. Views let each person focus on what matters to them. Components can live in multiple views (showing up in both the networking and application views, for example), and any changes to a component will reflect in every view.
Why we built fine-grained access control
As organizations scale with System Initiative, we've heard loud and clear that workspace-level approvals aren't always enough. Your security team might need exclusive approval rights for network changes, while your database admin should be the one approving database modifications.
For teams working in regulated environments (ISO 27001, SOC 2, HIPAA, GDPR), having these controls isn't just nice to have – it's essential for compliance. Instead of splitting your infrastructure across multiple repos or building custom approval systems, you can handle it all within SI.
How does it work?
We've designed fine-grained access control to be powerful yet intuitive. Here's a deeper look at how it functions:
Setting up view approvers
There are two simple ways to add approvers to views:
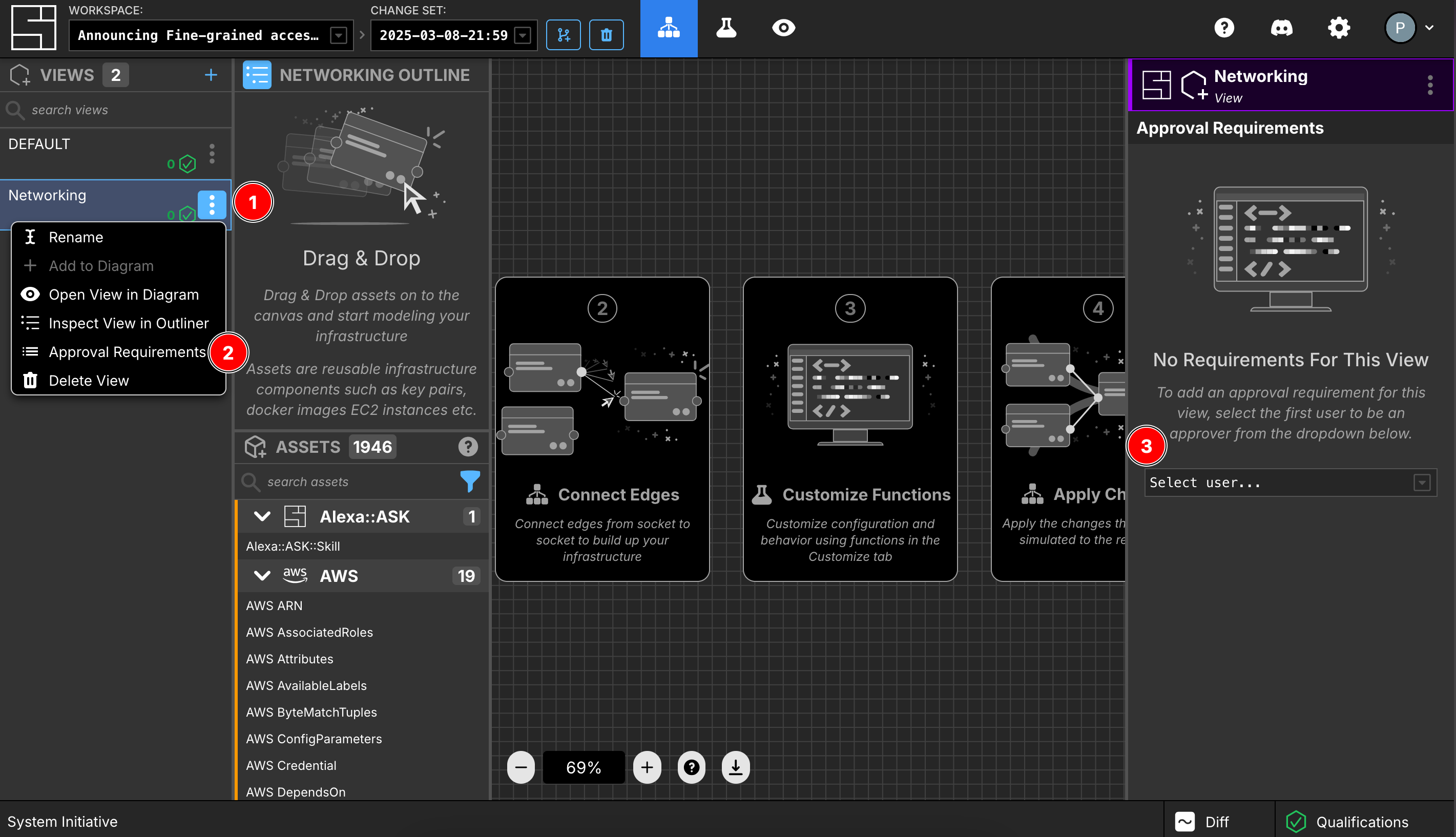
- From the view sidebar menu:
- Click the ellipsis (three dots) menu next to the view name in the sidebar (marked as
1in the screenshot) - Select "Approval Requirements" from the dropdown menu (marked as
2) - In the right panel that appears, use the dropdown to select team members to add as approvers (marked as
3)
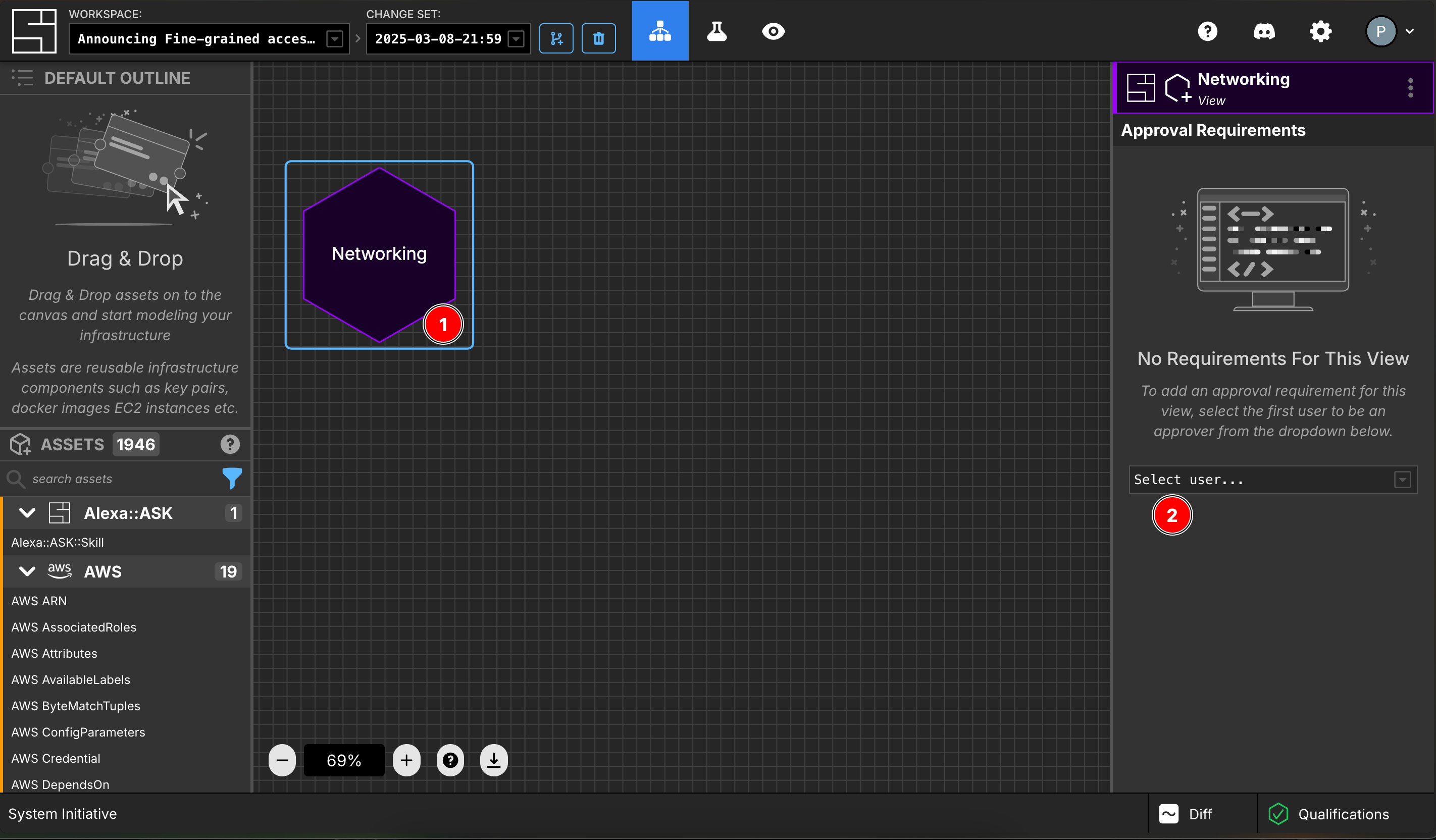
- From the diagram canvas:
- Click on the view's diagram object in your workspace (marked as
1in the screenshot) - Look for the Approval Requirements section in the right-hand panel
- Add approvers using the dropdown selector (marked as
2in the screenshot)
Approval Requirements Logic
We've built an intelligent approval system that calculates precisely who needs to sign off on changes:
- View-level precision: Approvers assigned to a view have authority over components within that view. When someone modifies the VPC in your Networking view, the networking approvers will be notified to review those changes.
- Precedence rules: View approvers take precedence over workspace approvers for components in their domain. This means your security team can be the final authority on security-related components, even if general workspace approvers exist.
- Cross-view changes: If a change spans multiple views (like connecting a database from one view to an application server in another), we automatically identify all affected views and require approval from each view's designated approvers. No changes slip through the cracks.
- Global element protection: Some things need centralized control. Workspace-level approvers retain authority over global elements like functions, schemas, and bindings that affect the entire workspace.
- Permission governance: All changes to the approval system itself (like adding or removing view approvers) require workspace-level approval, maintaining the security of your governance model.
- Change tracking integrity: We take approval integrity seriously - if someone makes additional changes after approval, that approval is automatically cleared. This prevents anyone from sneaking in extra changes after getting initial approval.
The approval workflow in action
Here's what the fine-grained approval process looks like in practice. In a workspace, Paul is the owner of the workspace and has made John and Brit workspace-level approvers. The workspace has several views:
- Networking view (with Scott as the designated approver)
- DNS view (no specific approver assigned)
- Application Infrastructure view (with Nick as the approver)
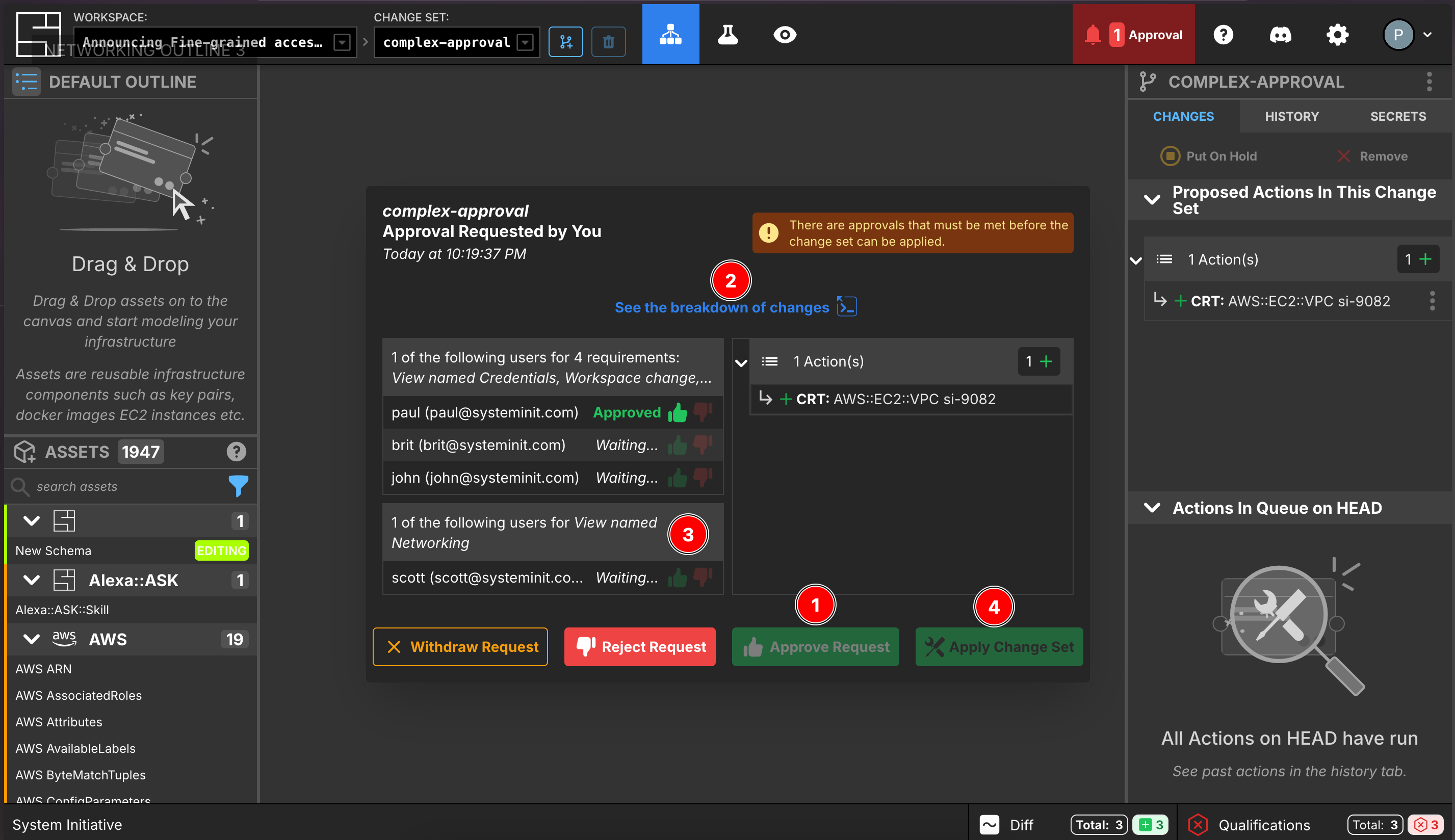 You can see, above, a complex approval requirement in progress. One of the workspace approvers needs to approve the request because there's a new view added and components changed in the default view. Paul has already provided that approval (marked as
You can see, above, a complex approval requirement in progress. One of the workspace approvers needs to approve the request because there's a new view added and components changed in the default view. Paul has already provided that approval (marked as 1 in the screenshot) on behalf of the workspace approvers.
The "See the breakdown of changes" button (marked as 2 in the screenshot) gives access to the audit log with a detailed list of all changes.
Scott has been requested for approval (marked as 3) specifically due to changes made in the networking view, where he's the designated approver.
Notice that the "Apply Change Set" button (marked as 4) remains unavailable until all required approvals are collected. Since Scott's approval is still pending, the changes cannot yet be applied.
This multi-level approval process ensures that all the right stakeholders sign off on changes before they take effect.
When can I use this?
Fine-grained access control is available for all users starting today. It works seamlessly with our existing Views and approval workflows. Based on your feedback, we're already planning future improvements to our permission systems.
Have questions or thoughts? Join us on Discord - I'm SI_Stack72 there, or just drop something in the #discussion channel. We'd love to hear how you're using this feature.

Paul Stack, Director of Product
Paul is an engineer turned product manager who is passionate about the Continuous Delivery and DevOps movements and how they are critical in helping businesses deliver value to their customers.